Many of us may be familiar with phishing — a malicious attempt to acquire sensitive information or by masquerading as a trustworthy source via email, text, pop-up message, etc. — but we still think of it as easy-to-spot spam messages from Nigerian princes. The truth is phishing has evolved to become much more advanced and effective.
Today's phishing messages can look incredibly legitimate, and they can appear to come from sources we know and trust.
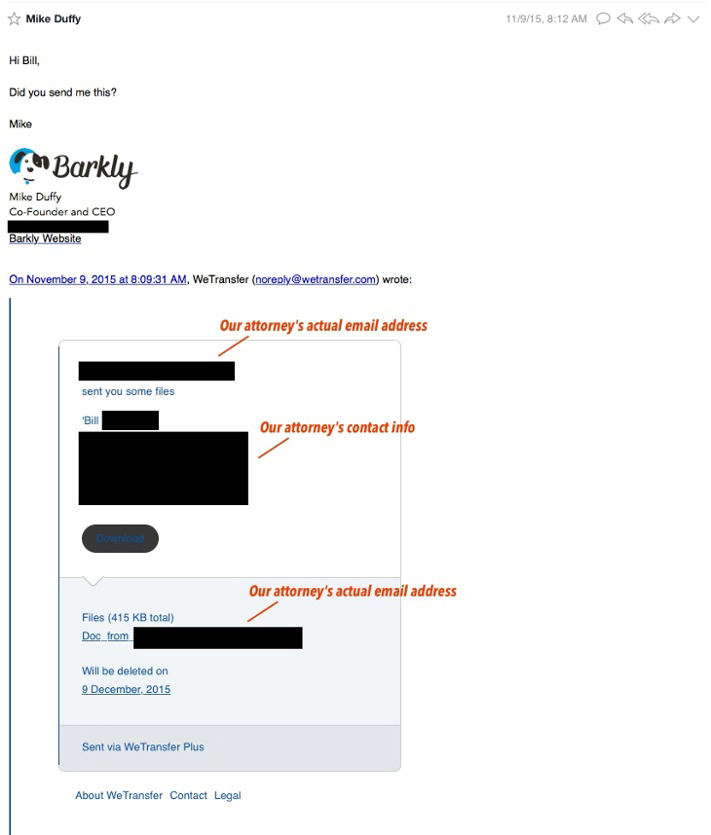
SAMPLE Phishing email below:
To the untrained eye, this message looks legit. It wouldn’t be out of the question for our lawyer to be reaching out to our CEO. Luckily for us, our CEO is used to keeping security top of mind and views any email even slightly out of the ordinary with scrutiny. In this case, he thought it was strange our lawyer would be sending him files out of the blue, as that’s something he’s never done before.
Instead of clicking on the download link, he called our lawyer (yes people still use phones to call people) asking him if he had in fact sent it. When our lawyer confirmed that he did not send the message Mike notified our research team, who analyzed the email and determined that it was indeed malicious.
Breaking Down the Phishing Attack:
The file the message linked to was cleverly named “Doc_from_[lawyer’s email address].com”. The “.com” is an old extension that can be substituted for .exe on Windows. The file itself was a malware executable with stereotypical malicious characteristics.
This was a clever phishing attack for a variety of reasons:
It used a real third party site (www.wetransfer.com) to host the malware.
“Wetransfer” requires no real identity proof and allows anyone to spoof an email. In this case the message From: field was our lawyer's real email address.
A casual glance may not have noticed the file was not an actual document (though a slight modification could make this an actual document by using a macro base downloader).
If Mike hadn't been skeptical it would not have taken much for this to infect his computer. The payload itself wasn’t particularly sophisticated — it was simply a repackaged version of [h p://www.win‐spy.com/.] But attacks often don't need to be overly sophisticated or stealthy. It only takes a few seconds of actual processing time to do enough damage that the machine needs to be re‐imaged. It often comes down to how quickly something like this is discovered and how quickly it can be contained.
Lessons Learned
As this case shows, phishing is something that we should all be taking seriously.
Companies need to invest in proper cybersecurity awareness training to help employees know how to recognize warning signs and exercise caution.
Even then, it is very likely that you will have to deal with a successful phishing attack at some point. All it takes is one click.
Ultimately organizations need to get to a point where email is not used as a file transfer mechanism. With so many better ways to share content today, it’s a lot easier to see that something is out of the ordinary when you have instituted a standard means for sharing content both internally and with your partners (in this case none of us had heard of wetransfer so that in itself was suspicious).
In the meantime, a simple but powerful tip is don’t be so quick to click, especially when handling documents shared or proxied through email.


Leave a comment!
You must be logged in to post a comment.